
The reality is that, despite it being a requirement of most HPC customers, HPC vendors are not doing a lot when it comes to security when there is a lot of opportunity to leverage this to differentiate.
Good security is about dissecting something in order to understand how it works and then looking for ways to manipulate in order to facilitate unintended functionality. As long as that principle exists security can apply within any environment.

A vulnerability was identified within IBM Spectrum LSF which made it was possible to impersonate other users when submitting jobs for execution. Additionally, it was found to be possible to impersonate and execute jobs as root, even where root job submission is disabled.
An insecure update mechanism on DDN SFA devices allows for privilege escalation to root.
DDN SFA devices have default SSH keys in place which can be used to gain access.
A command injection vulnerability in GPFS / Spectrum Scale allows attackers to escalate privileges to root

The VX binary on SGI ICE-X supercomputers can be used to escalate privileges to root.
It is possible for users of ICE-X supercomputers to gain access to backups of system configuration databases.
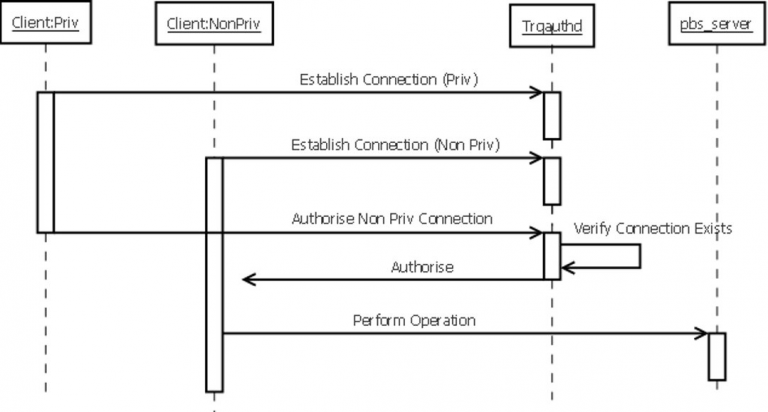
It is possible to bypass authentication within Moab in order to impersonate and run commands/operations as arbitrary users. The issue is believed to affect all versions of Moab prior to versions 7.2.9 and Moab 8.
Moab provides two methods to authenticate messages sent by users (e.g. job submissions). The default scheme which is widely used is insecure and can be circumvented in order to impersonate other users and perform operations on their behalf.



